Blog series
- Starting with Windows 365
- Getting started with Windows 365 Business
- Windows 365 Enterprise – AAD Join
- Windows 365 Enterprise – Hybrid Join
- Windows 365 Enterprise – Custom Images
In the previous article we deployed Windows 365 cloud pc Azure AD only. In this article we will deploy a cloud pc as Hybrid join. So what is hybrid join? Hybrid joining the machine joins the machine to both the Azure AD as well as the Active directory. When would you choose for a hybrid join set up? There are a couple of scenarios when you would want to choose for a hybrid set. For example you are still highly relying on configuring your devices with Group policies, or you have some legacy application that require machine authentication, or you want to use the hybrid join option in your Conditional access policies. All are valid reasons to use hybrid join. In my opinion Azure AD joining is preferable because it eliminates some moving parts in your configuration. These parts can break time to time so not having them will make your life easier.
When you hybrid join a machine the machine is first joined to the Active Directory and then synchronized to Azure AD. This is done via a certificate. AAD connect by default does not synchronize the certificates and therefor you need to adjust AAD connect for hybrid join.
Configure AAD Connect
So, the first step is to configure hybrid Join in AAD connect. Open AAD connect and select Configure device options. You will see an overview screen where you can select Next. Enter your Azure AD global administrator credentials. Select Configure Hybrid Azure AD Join and Next. Then you select Windows 10 or later domain-joined devices and select Next. You now need to add the SCP configuration. This SCP contains information for the device about where to look for its information as it needs to be joined to Azure. Here you select your forest, authentication service which is most likely Azure Active Directory and select add to enter your enterprise admin credentials. When you hit next some final validations will be done and finally you can choose Configure. Later I will show how to validate the Hybrid Join and what process actually got into motion. Also, if you are planning to deploy the cloud pcs in a specific OU make use the OU is also in sync scope. The OU needs to syn the attributes to Azure AD.

Azure Network Connection
Now AAD connect is ready you can configure Windows 365 for hybrid join. In order to do so go to endpoint.microsoft.com and choose devices and Windows 365. There you select Azure network Connection.
On the tab select create and choose Hybrid Azure AD Join. Enter a name which tells you something about the connection, for example what the vnet is you are connecting to. Select the subscription that has the vnet and select the subnet you want your machines to join to. It’s important that your vnet is in the same region as where you want to deploy your cloud pcs as vnet are bound to a specific region. Select next and create the connection. Make sure your account has the appropriate permissions on the subscription (Owner) and within Endpoint manager.

With Hybrid join you need to add additional domain information. Enter the AD DNS name, optional the OU where the devices should be joined into (make sure this OU is syncing to Azure AD), and credentials of a user which has sufficient rights to join multiple pcs.

Microsoft will start running some checks and if all went well, you will get a checks success status. Note that you can have both join types of Azure AD and Hybrid Join pointing to the same vnet and subnet.

Provisioning policies
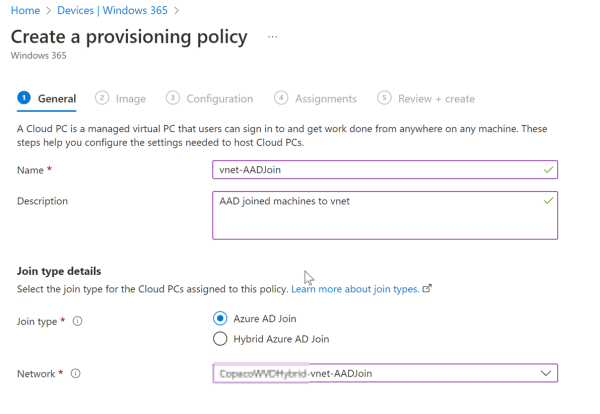
The next step should be creating a Provisioning Policy. These policies determine how the Windows 365 pc should be created. From the Devices section select Provisioning policies and select create policy. Enter a name and description. For Join type make sure to select Hybrid Azure AD Join. So, choose for Azure network connection and select the hybrid network connection you just created in the previous step.

At the image tab pick a gallery image, or a custom image if you have one. Check this article if you’re interested in how to create a custom image. At the configuration tab select the language and region. This will automatically install the required language packs on the machine. For additional services you may choose Windows Autopatch. Windows Autopatch manages updates for you. It’s not really a Window 365 services but you can read more about it in this blog Blog | Get current and stay current with Windows Autopatch | Tech Community (microsoft.com)
Finally assign the policy to a group which contains your users. When you have finished creating the provisioning policy you are basically set. When a user has a valid license (a Windows 365 enterprise and a license containing Intune) and is a member of the group which is assign the provisioning policy the cloud pc will be created.
Now I assign the following licenses to my test user in order to start the provisioning of the device. My test user Mickey has 2 licenses: a Microsoft 365 E3 and the Windows 365 Enterprise 2 vCPU, 8 GB, 256 GB license.
Hybrid Join
So how is a device hybrid joined? This process is pretty interesting and does not only apply to Windows 365 but also to normally hybrid joining clients. Hybrid joining set a scheduled task in motion. You can find the scheduled task in \Microsoft\Windows\Workplace Join called Automatic-Device-Join, which is triggered from in this case an event Microsoft\Windows\User Device Registration\Admin. The scheduled task calls upon dsregcmd.exe. One of the first steps in this process is for the computer to create a userCertificate.

This certificate is then uploaded to Azure AD. This is why you needed to reconfigure AAD connect for this process to work. Without the certificate the device won’t synchronize with AAD.

Sometimes the hybrid join process won’t kick off, you can manually start the process by running the scheduled task (\Microsoft\Windows\Workplace Join\ Automatic-Device-Join) or by running dsregcmd /join from PowerShell.
Also verify that the pc shows up as hybrid joined in the endpoint manager portal.